The Security Checklist
The Security Checklist
Blog Article
When you are blogging, there are a number of things that can go right and a variety of things that can likewise fail. There are some significant errors that you require to be preventing when you are blogging. Discover what these are so that these things don't occur with your blog site.
Not having control of your blog site is a substantial mistake. Many begin with blogs on free platforms. These are much easier considering that you don't pay anything and it's already established. The issue is that eventually these can be randomly erased for any factor. You need to get a blog onto your own site to be secured so you have control of whatever.
So, the drive to consume isn't under your direct control. Can you think of if it was? Think about all the tasks you are expected to remember to do. The number of times have you forgotten to get the trash, foot the bill, or select up a gallon of milk en route home from work? Absolutely nothing truly bad takes place if you forget any of these. Forgetting to consume cybersecurity regulations means death. That's why consuming needs to be a drive.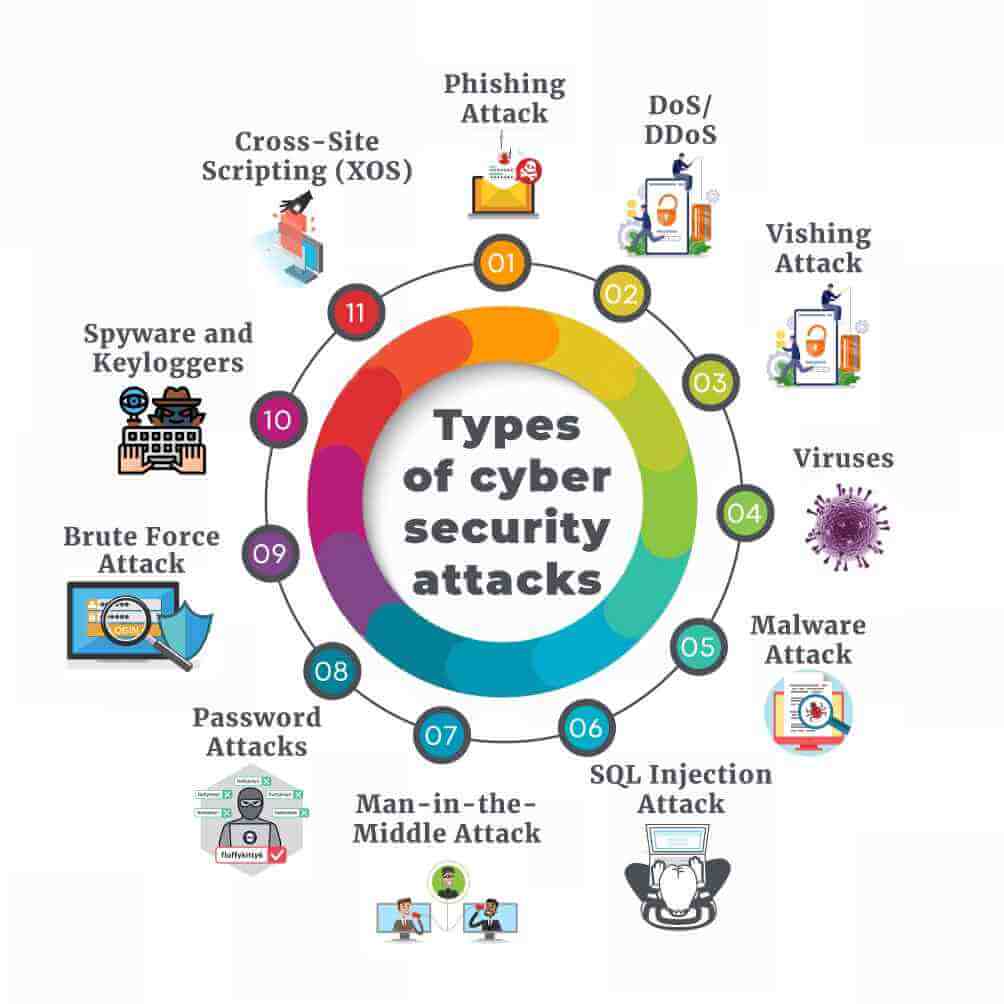
An Amazon tablet with a glare-proof screen will be another power function. Some tablets, when subjected to light, reflect a lot light to the point that the reader discovers it challenging to read and see whatever is on the screen. A glare-proof screen would certainly optimize the user and enhance's reading experience.
Before I get into the particular infections Cybersecurity Threats and malware, a little bit of background is required. Believe it or not, the McAfee computer security business states that at any provided point in time, there are thousands of active infections contaminating computers. Thousands! And many computer system users do not even know it!
We humans are exceptional at acquiring weight. It takes a lot of training to end up being a world class sprinter, yet the majority of people can become obese with absolutely no training at all! It's a natural skill we have.
Have you carried out a RF video sweep for surprise cameras. Visitor's and students can set up surprise camera inside your school and learn when you go into a location. Some students install and even wear concealed electronic cameras to record illegal images of ladies undressing. Do the sweep, you may be amazed at what you discover.
I hope you've found this short article on the leading 5 infections and malware of usage. Infections can be a really costly problem for your company. By installing and keeping anti-virus software upgraded and performing at perpetuity, you will considerably minimize your and your organizations opportunities for ending up being a victim.